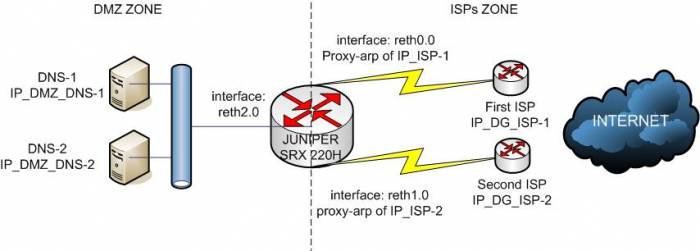
1. Конфигурация двух security zones на Juniper:
{primary:node1}[edit]
set security zones security-zone ISPs interfaces reth0.0
set security zones security-zone ISPs interfaces reth1.0
set security zones security-zone ISPs address-book address A_ISPs_DNS-1 IP_ISP-1/32
set security zones security-zone ISPs address-book address A_ISPs_DNS-2 IP_ISP-2/32
set security zones security-zone DMZ interfaces reth2.0
set security zones security-zone DMZ address-book address A_DMZ_DNS-1 IP_DMZ_DNS-1/32
set security zones security-zone DMZ address-book address A_DMZ_DNS-2 IP_DMZ_DNS-2/32
2. Конфигурация security policies
{primary:node1}[edit]
set security policies from zone DMZ to zone ISPs policy DMZ_to_ISPs match source-address A_DMZ_DNS-1
set security policies from zone DMZ to zone ISPs policy DMZ_to_ISPs match source-address A_DMZ_DNS-2
set security policies from zone DMZ to zone ISPs policy DMZ_to_ISPs match destination-address any
set security policies from zone DMZ to zone ISPs policy DMZ_to_ISPs match application junos-dns-tcp
set security policies from zone DMZ to zone ISPs policy DMZ_to_ISPs match application junos-dns-udp
set security policies from zone DMZ to zone ISPs policy DMZ_to_ISPs then permit
set security policies from zone ISPs to zone DMZ policy ISPs_to_DMZ match source-address any
set security policies from zone ISPs to zone DMZ policy ISPs_to_DMZ match destination-address A_ISPs_DNS-1
set security policies from zone ISPs to zone DMZ policy ISPs_to_DMZ match destination-address A_ISPs_DNS-2
set security policies from zone ISPs to zone DMZ policy ISPs_to_DMZ match application junos-dns-tcp
set security policies from zone ISPs to zone DMZ policy ISPs_to_DMZ match application junos-dns-udp
set security policies from zone ISPs to zone DMZ policy ISPs_to_DMZ then permit
3. Отключение DNS security alg (Без этой строчки работать будет только через одного проайдера.)
{primary:node1}[edit]
set security alg dns disable
4. Конфигурация двух routing instance. Для каждого проайдера своя routing instance
{primary:node1}[edit]
set routing-instances INS_ISP-1 instance-type forwarding
set routing-instances INS_ISP-1 routing-options static route 0.0.0.0/0 next-hop IP_DG_ISP-1
set routing-instances INS_ISP-2 instance-type forwarding
set routing-instances INS_ISP-2 routing-options static route 0.0.0.0/0 next-hop IP_DG_ISP-2
5. Конфигурация шлюза по умолчанию.
{primary:node1}[edit]
set routing-options static route 0.0.0.0/0 next-hop IP_DG_ISP-1
set routing-options static route 0.0.0.0/0 qualified-next-hop IP_DG_ISP-2 preference 100
6. Конфигурация policy routing
{primary:node1}[edit]
set firewall family inet filter PRULE_ISP-2 term TERM1 from address IP_ISP-2/32
set firewall family inet filter PRULE_ISP-2 term TERM1 then routing-instance INS_ISP-2
set firewall family inet filter PRULE_ISP-2 term default then accept
7. Применение policy routing на интерфейсе, подключенном к ISP-1
{primary:node1}[edit]
set interfaces reth0 unit 0 family inet filter output PRULE_ISP-2
8. Конфигурация PPROXY-ARP
{primary:node1}[edit]
set security nat proxy-arp interface reth0.0 address IP_ISP-1/32
set security nat proxy-arp interface reth1.0 address IP_ISP-2/32
9. Конфигурация PAT (Destination NAT)
{primary:node1}[edit]
set security nat destination pool DMZ_DNS-1 address IP_DMZ_DNS-1/32
set security nat destination pool DMZ_DNS-1 address port 53
set security nat destination pool DMZ_DNS-2 address IP_DMZ_DNS-2/32
set security nat destination pool DMZ_DNS-2 address port 53
set security nat destination rule-set ISPs_to_DMZ from zone ISPs
set security nat destination rule-set ISPs_to_DMZ rule PAT_DNS_1 match destination-address IP_ISP-1/32
set security nat destination rule-set ISPs_to_DMZ rule PAT_DNS_1 match destination-port 53
set security nat destination rule-set ISPs_to_DMZ rule PAT_DNS_1 then destination-nat pool DMZ_DNS-1
set security nat destination rule-set ISPs_to_DMZ rule PAT_DNS_2 match destination-address IP_ISP-2/32
set security nat destination rule-set ISPs_to_DMZ rule PAT_DNS_2 match destination-port 53
set security nat destination rule-set ISPs_to_DMZ rule PAT_DNS_2 then destination-nat pool DMZ_DNS-2
10. Конфигурация NAT
{primary:node1}[edit]
set security nat source pool EXT_DNS-1 address IP_ISP-1/32
set security nat source pool EXT_DNS-2 address IP_ISP-2/32
set security nat source rule-set From_DMZ_to_ISPs from zone DMZ
set security nat source rule-set From_DMZ_to_ISPs to zone ISPs
set security nat source rule-set From_DMZ_to_IMT_IP rule NAT_DNS-1 match source-address IP_DMZ_DNS-1/32
set security nat source rule-set From_DMZ_to_IMT_IP rule NAT_DNS-1 then source-nat pool EXT_DNS-1
set security nat source rule-set From_DMZ_to_IMT_IP rule NAT_DNS-2 match source-address IP_DMZ_DNS-2/32
set security nat source rule-set From_DMZ_to_IMT_IP rule NAT_DNS-2 then source-nat pool EXT_DNS-2
11. Сохранение и применение созданной конфигурации
{primary:node1}[edit]
commit